Information security management
As a leading developer of test instruments and equipment, Chroma is committed to deepening its information security architecture through innovative technology and close collaboration with key partners, protecting the Company’s critical information assets and customer data security. Facing increasingly severe cybersecurity threats, we obtained ISO 27001 information security certification in January 2022 and implemented a cycle of continuous improvement through the Plan-Do-Check-Act (PDCA) model. Furthermore, in December 2024, we completed the ISO 27001:2022 version upgrade verification audit, which also extended the certification scope to include subsidiary ADIVIC Technology Co., Ltd. and the Netherlands branch.
Information security management framework

To enhance group-wide security management, Chroma ATE Inc. reports the implementation status of information security management to the Board of Directors on a regular basis, with the most recent report submitted at the Board meeting on October 31, 2024. The Information Security Management Office currently consists of the Information Security Audit Team, the Information Security Management Team, the Information Security Emergency Response Team, and designated information security management contacts within each business unit.
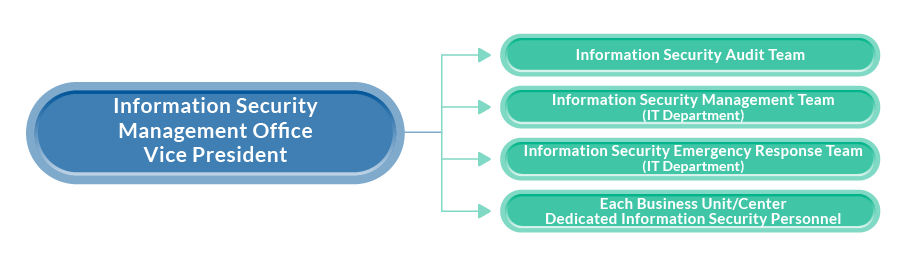
The Information Security Management Office is responsible for promoting the information security management system and executing various information security management tasks. It convenes at least one management review meeting per year to regularly review the handling of issues raised in previous audits and to examine both internal and external issues related to the information security management system, ensuring their integration into the management system.
Information security management action

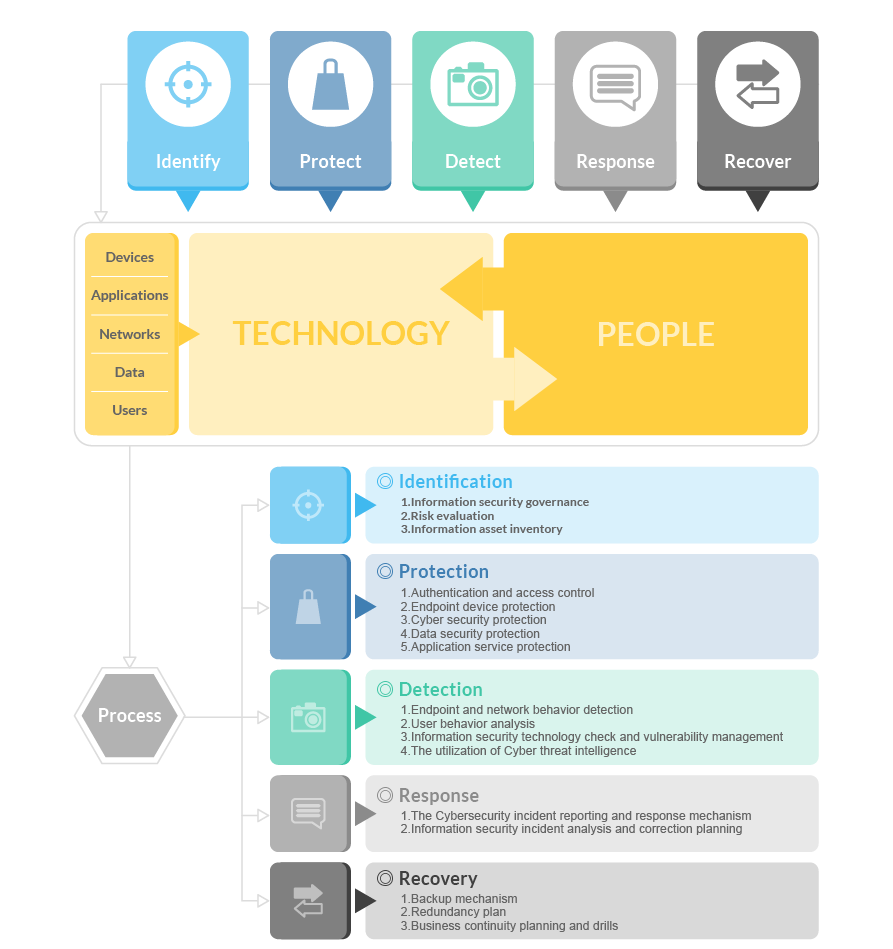
According to Chroma’s information security implementation model, the specific actions of information security management are as follows:
1. Cybersecurity:
Introduce advanced detection technologies to perform network monitoring, block malicious cyberattacks, and collect cybersecurity threat intelligence to prevent the spread of computer viruses.
2. Device Security:
(1) Enhance endpoint antivirus and scanning mechanisms to prevent ransomware and malicious software.
(2) Strengthen email systems to detect malicious software, trojan attachments, and phishing emails.
(3) Monitor internet behavior and block highly dangerous malicious websites, malicious links, or file downloads.
3. Application Security:
Establish security inspection procedures, evaluation standards, and improvement targets for application development processes. Continuously strengthen security control mechanisms for applications and patch potential vulnerabilities.
4. Data Protection:
Establish user password management mechanisms and network security zone segmentation to maintain access control and data security.
5. Account Management and Employee Education & Training:
Establish password policies and require periodic updates, and regularly conduct employee information security awareness education and testing.
6. Information Security Incident Management:
Continuously monitor and collect records of information security protection operations, collect and analyze cybersecurity intelligence, and establish information security incident reporting and handling procedures.
Chroma's information security executive models
Information security management actions are based on three key elements—personnel, technology, and processes—following the five aspects of information security management: Identify, Protect, Detect, Respond, and Recover. Combined with various information security management solutions and processes, and adopting the concept of information security maturity, the life cycle of network security risk management is covered to establish assessment benchmarks and further enhance the level of cybersecurity defense.
The performance of information security management in 2024

Conducted one drill on data center infrastructure backup functionality, including ICT infrastructure.
Executed one business continuity drill per year covering 10 major items, including backup functionality or backup mechanisms of key information systems used in daily operations.
Completed 67 backup data restoration verifications to ensure the availability of backup data.
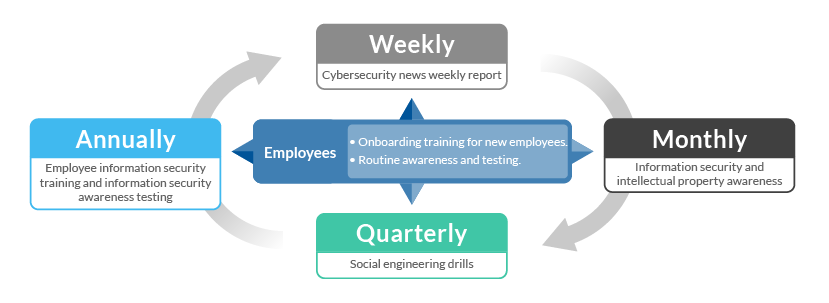
Conducted 2 internal and external system vulnerability scans and 4 social engineering drills.
Information personnel completed 7 information security education training sessions (totaling 13 hours), and information supervisors attended 8 hours of external training courses.
Conducted weekly information security incident awareness campaigns (49 sessions in total) to raise employee cybersecurity awareness.
General employee information security awareness education training conducted once (2 hours). Monthly information security policy awareness and information security awareness testing are conducted to improve employees’ response and alertness to information security risks. The Information Security Management Office has implemented various stages of the following actions:
Upon reviewing the 2024 information security implementation status of each unit, there were no information security incidents that harmed the Company, nor any verified complaints from external parties (such as customers), nor any complaints from regulatory authorities.
Annual audits and supervision of information security management are conducted by an external ISO 27001 auditing organization.
Contact of Information Security Office
Employees who identify information security risks can immediately contact the designated personnel of the Information Security Office: